The FRI-Binus paper [DP24] discusses the Additive FFT algorithm based on Subspace Polynomial and provides a perspective to understand the Additive FFT algorithm based on Novel Polynomial Basis in [LCH14] using odd-even decomposition. This article directly introduces the Subspace Polynomial, and then introduces the Additive FFT algorithm from the perspective of odd-even decomposition. This article omits the definition of Normalized Subspace Polynomial for easier understanding. Normalization only affects the performance of the FFT algorithm and has no essential difference from the simplified algorithm introduced in this article.
Notes on Binius (Part II): Subspace Polynomial
Notes on FRI-Binius (Part I): Binary Towers
Binary fields possess elegant internal structures, and Binius aims to fully utilize these internal structures to construct efficient SNARK proof systems. This article mainly discusses the Binary Fields that Binius relies on at its core and the construction methods of Extension Towers based on Binary Fields. Binary Fields provide smaller fields and are compatible with various tool constructions in traditional cryptography while also being able to fully utilize optimization of special instructions on hardware. There are two main advantages to choosing Extension Towers: one is that the recursive Extension construction provides a consistent and incremental Basis selection, allowing Small Fields to be embedded into Large Fields in a very natural way; the other advantage is that multiplication and inversion operations have efficient recursive algorithms.
Trust Wallet's Fomo3D Summer: Fresh Discovery of Low Entropy Flaw From 2018

In July 2023, numerous ETH wallets were hacked, leading to an investigation that uncovered a low entropy flaw in Trust Wallet dating back to 2018. This vulnerability, linked to a predictable random number generation issue in Trust Wallet’s code, resulted in easily guessable wallet keys. The exploit affected over 2100 victims, causing a loss of over 1360 ETH and potentially millions of dollars across various blockchains. Evidence suggests that most affected users were Trust Wallet users or users of Trust Wallet fork products. This incident highlights the importance of secure random number generation in wallet security.
The 'Input Aliasing' bug caused by a contract library of zkSNARKs
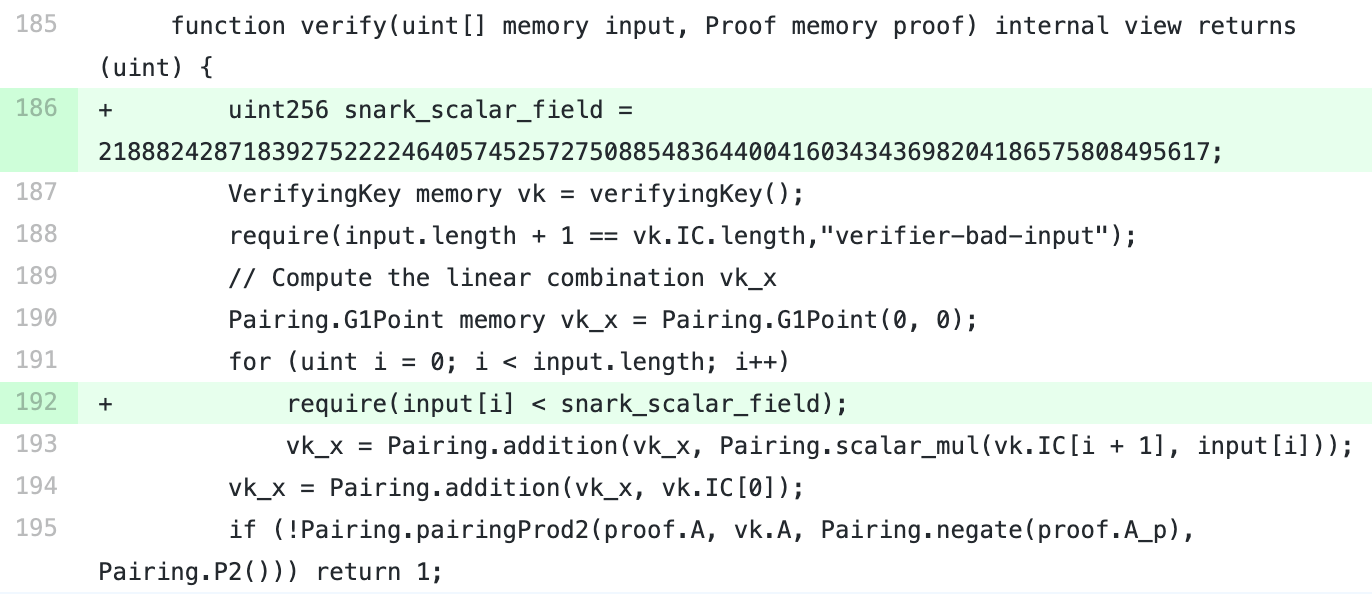
Many zero-knowledge proof projects are threatened by attacks like faking proof, double spending and replaying due to the ‘Input Aliasing’ bug caused by a contract library of zkSNARKs. This applies to many Ethereum open-source projects as well, including 3 most popular zkSNARKs library - snarkjs, ethsnarks, ZoKrates and 3 topical mixcoin apps - hopper, Heiswap, Miximus.
'Move' Programming Language: The Highlight of Libra

Among publications of Libra, the most attractive thing would be the brand new ‘Move’ programming language. After the first glance at ‘Move’ whitepaper, we came to the idea that this is the future of smart contract language.